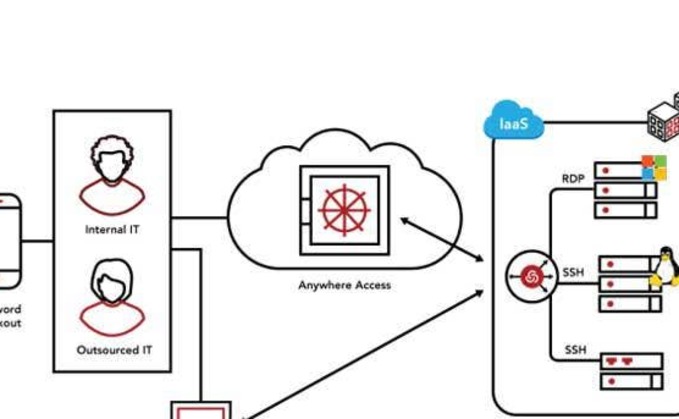
Identity Access and Management (IAM) tools are not just a nice-to-have extra layer of security to have within an infrastructure – they are critical. Users are logging into many SaaS applications, from many locations and across multiple devices. That access must be managed.
There are three vital components to IAM: authentication, authorization and access management. Okta is a leading IAM provider but there are others who have solutions ideal for the midmarket. MES Computing asked several companies that are prominent in the IAM space, why their solution is a good fit for the midmarket. CyberArk and ManageEngine provided responses that not only showed why their solutions are ideal for midmarket organizations, but what IT leaders should look for in an IAM solution:
CyberArk Identity Security Platform
What differentiates CyberArk from competitors?
CyberArk says it is the "the pioneer of privileged access management," in a statement to MES Computing. "Over the years, we have built upon that foundation to become the global leader in identity security," the statement continued.
At the center of the CyberArk Identity Security Platform are intelligent privilege controls that "seamlessly secure human and machine identities" across hybrid and multi-cloud workloads. Continuous threat detection and prevention, zero trust, and least privilege enforcement are some of the features securing "access for any identity – human or machine – to any resource or environment from anywhere using any device."
Why is CyberArk an ideal solution for midmarket companies?
As an SaaS solution, it provides companies with a balance of security, productivity and cost. "It's ideal for midmarket organizations as it allows them to scale their cybersecurity investment to match current business needs," the company said.
CyberArk also pointed to the growing trend of midmarket organizations using MSPs and MSSPs to assist with their critical business and IT operations.
"CyberArk's robust partner ecosystem and tech alliances allows companies to partner and integrate with traditional resellers, integrators, MSP, MSSPs and other leading technologies that best suit their business needs. For MSPs and MSSPs to better serve their customers, CyberArk launched an MSP Console that allows our partners to seamlessly view, monitor and administer all MSP-controlled CyberArk customer environments from a single console," the company said.
What is the most important factor companies should consider when looking for an IAM solution?
According to CyberArk:
"Boundaries are gone. Identities are the front lines of defense, and the total number of identities is growing at an accelerated rate. ‘Privileged users' are no longer just IT admins – over 50% of all employee identities today have access to sensitive systems and data that attackers can easily exploit. In this environment, every identity at any access point is a gateway to an organization's most valuable resources.
When considering an IAM solution, security leaders must recognize that achieving and maintaining control of every identity is the key to stopping most modern attacks. The sheer amount of identities is overwhelming. They range from workforce, business partners and customers to endpoints and infrastructure. The solution a company picks needs to be able to grow easily and quickly to keep every single identity that touches critical business data safe."
ManageEngine AD360 (for on-prem) and Identity360 (for cloud)
What differentiates ManageEngine's IAM solution from competitors?
What differentiates ManageEngine's IAM platform is its "unified identity fabric approach that bridges traditionally siloed IAM capabilities across identity governance, access management, and security," said Jay Reddy, senior technology evangelist at ManageEngine.
Automation of routine identity processes, intelligent access certification recommendations, and constant monitoring and remediation of identity risks are some key features.
"This ML-drive intelligence reduces operation overhead for lean IT teams," Reddy said.
He said that a key strength of the platform is its "independent, neutral architecture that seamlessly integrates with any technology stack—cloud, on-premises, hybrid environments. This flexibility ensures organizations can adopt the best solution without constraints."
According to Reddy, the platform balances "robust security controls with a focus on digital employee experiences through features like context-aware adaptive MFA, single digital identity, self-service access requests, and approval workflows."
ManageEngine, he said, is at the "forefront of AI and identity intelligence, with a roadmap that includes autonomous configuration drift correction, prescriptive access intelligence, and identity security posture management. These AI-driven features will further enhance visibility, reduce manual effort, and strengthen identity security postures."
Why is ManageEngine's IAM solution ideal for midmarket companies?
"ManageEngine's IAM platform is tailored for the unique needs of midmarket organizations," Reddy said. "As these companies experience rapid growth, the solution scales effortlessly to support expanding user bases without performance degradation or significant overhead.
The unified design streamlines complex identity processes, reducing manual effort for lean mid-market IT teams through intelligent automation, centralized administration, and comprehensive reporting/analytics.
Reddy said that the platform's identity threat detection and response engine constantly monitors identities, "automatically detecting, and mitigating risks, which is crucial for midmarket teams managing expansive identity landscapes with limited staff."
He also said that ManageEngine provides flexible licensing that "allows companies to align spending with their current requirements while retaining flexibility to expand as business needs evolve."
"For mid-market companies, ManageEngine's modular design and licensing aligns with typical budgets, allowing them to start with essential capabilities and scale as requirements evolve. The cloud-native architecture of Identity360 enables seamless expansion without additional infrastructure costs," he said.
What is the most important factor companies should consider when evaluating an IAM solution?
According to Reddy:
"The primary consideration should be how well an IAM solution supports the organization's long-term strategic roadmap and requirements for IT infrastructure, workforce enablement, customer engagement models, and overall security posture.
An ideal IAM platform must provide a unified, comprehensive approach spanning identity governance, provisioning, access management, and data access governance, rather than a collection of disjointed tools. This unified visibility and control simplify complex identity programs.
Seamless integration across the entire existing and future technology footprint—be it cloud, on-premises, hybrid environments, or third-party applications—is vital to avoid disruptive rip-and-replace initiatives as the IT landscape evolves.
Scalability to support evolving business growth, AI-driven intelligence to reduce manual effort, and the ability to customize policies/workflows as requirements change are essential for long-term relevance and ROI.
Finally, companies must prioritize solutions from vendors with proven expertise across identity security domains, robust implementation support, consistent innovation roadmaps, and a track record of protecting customers against emerging identity-based threats and cyber risks."


















